


📖 Estimated reading time: 2 min
Sysdig enterprise aims to analyze the security of Kubernetes clusters and all their integrations, such as registries and CI/CD belts. This solution can also prevent abuse through the use of policies, as well as indicating what can be improved in your cluster in order to increase the overall reliability levels of the environment.
The solution is based on interactive dashboards, of which the platform already has a wide range. It is also possible to create customized dashboards.
This kind of solution is especially important for financial institutions, such as banks, insurance companies and investment firms.
Some niche markets have strict security standards.
This article will be divided into 3 parts. In this first part we’ll talk a bit about Sysdig, and in the other two I’ll show you how to install and configure sysdig agents on OpenShift clusters, which is Red Hat’s Kubernetes platform solution. The procedure is the same for different Kubernetes clusters, so the information will probably be useful to you.
Sysdig Monitor is a solution that automatically assesses the health of Kubernetes environments. In reality, it also works with Linux servers, but in this article we’ll only be talking about Kubernetes.
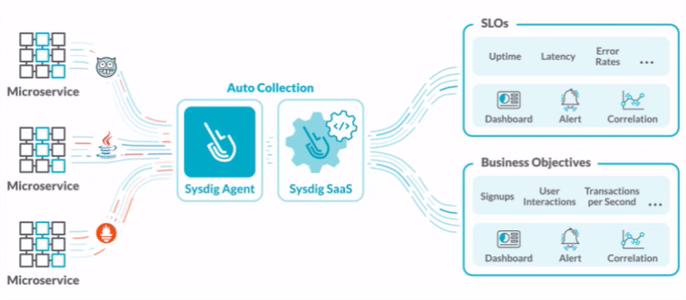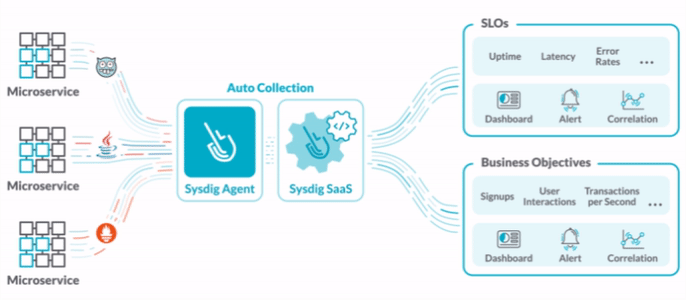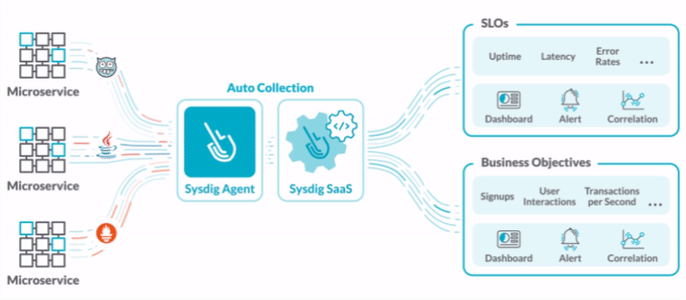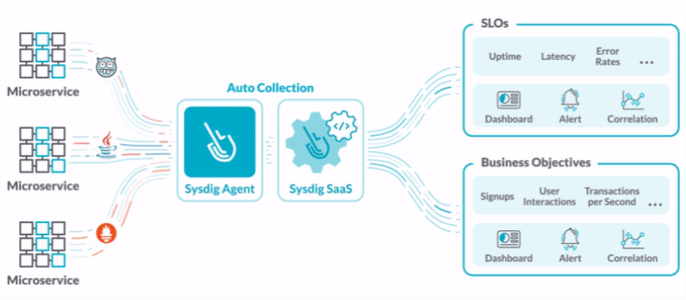
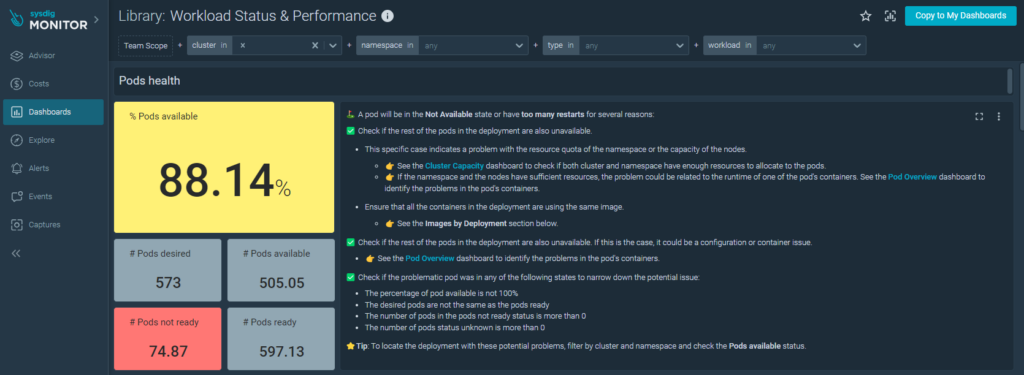
Let’s explore some of the dashboards provided.
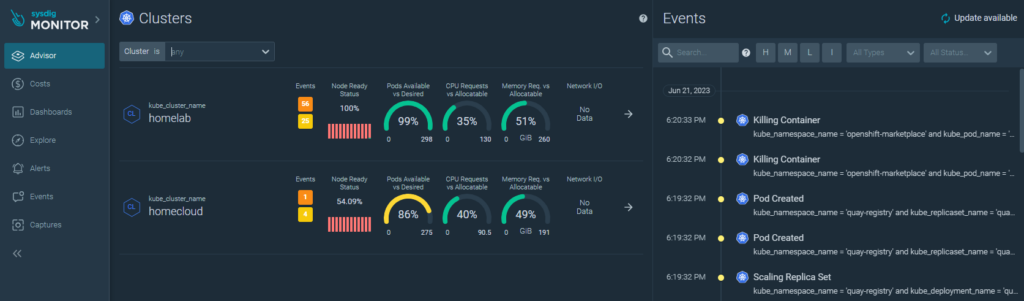
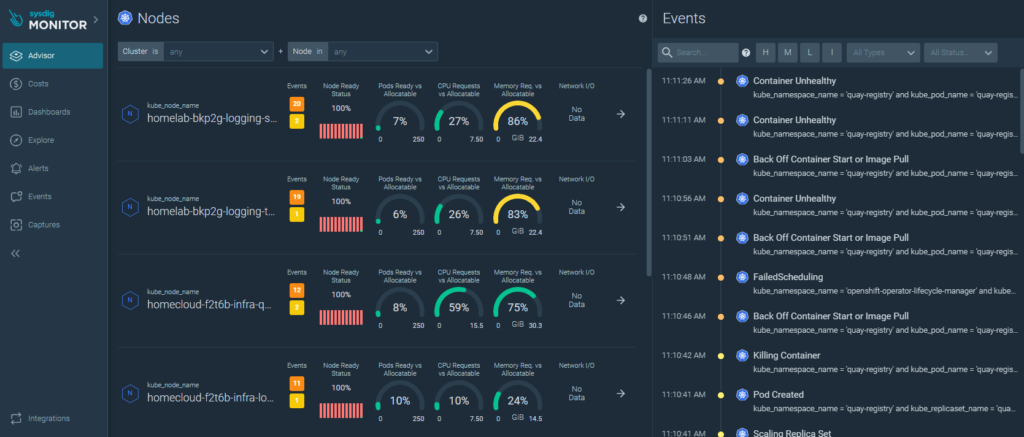
Individual details about the platform’s nodes (servers):
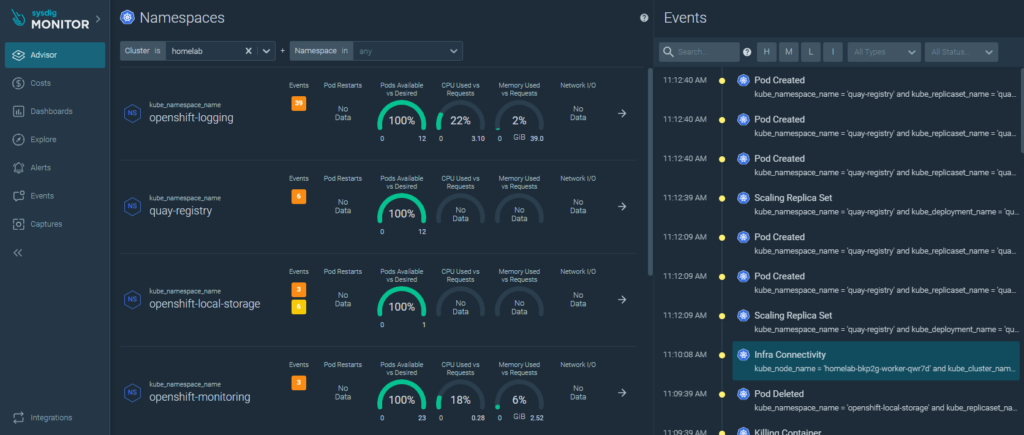
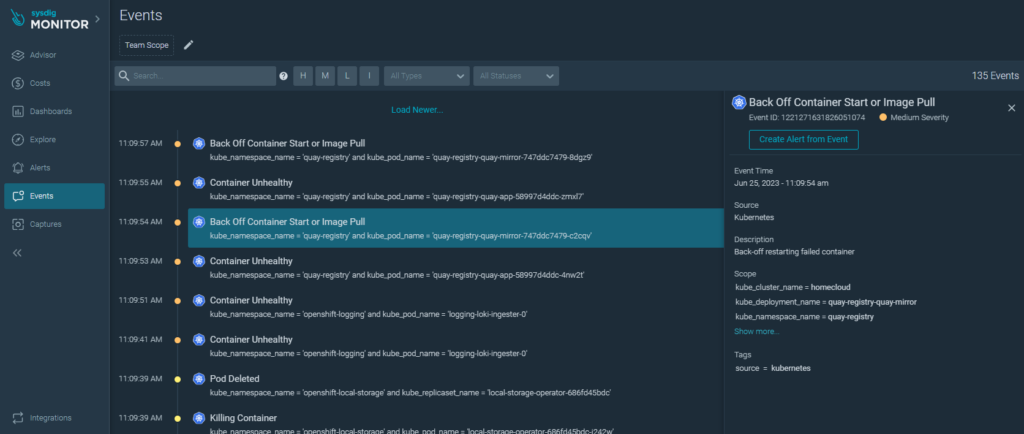
Details of events of interest according to namespace can be consulted:
Events:
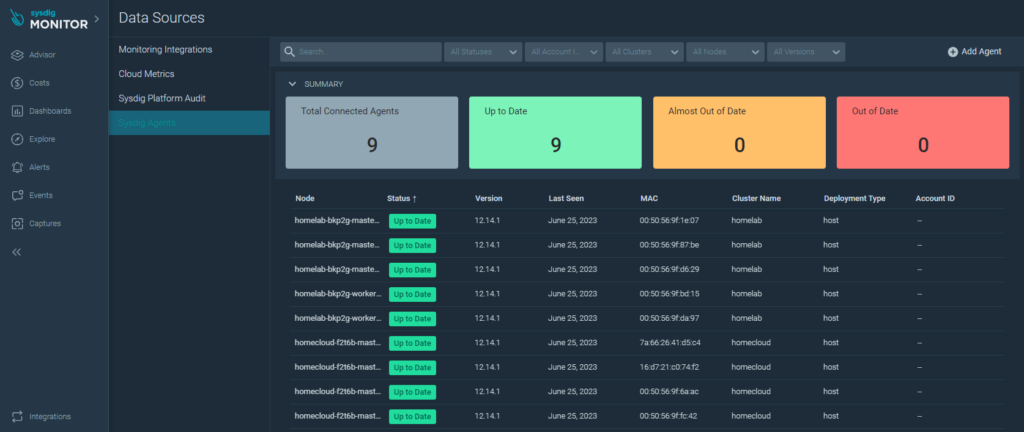
The agent itself is monitored:
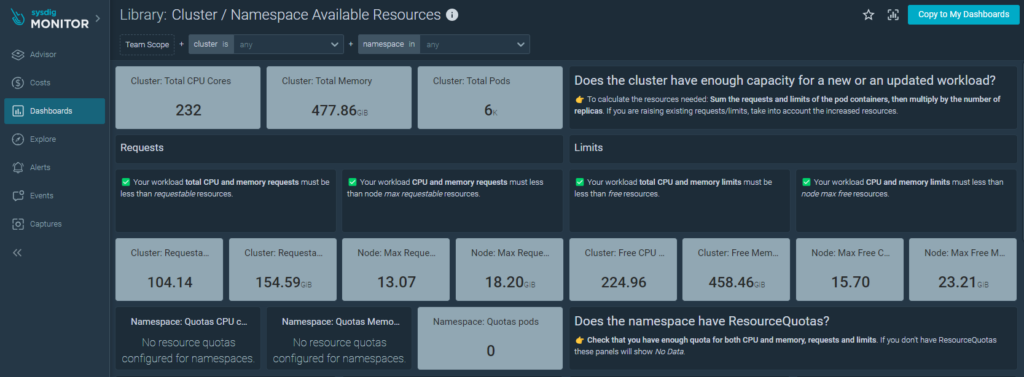
Resource consumption:
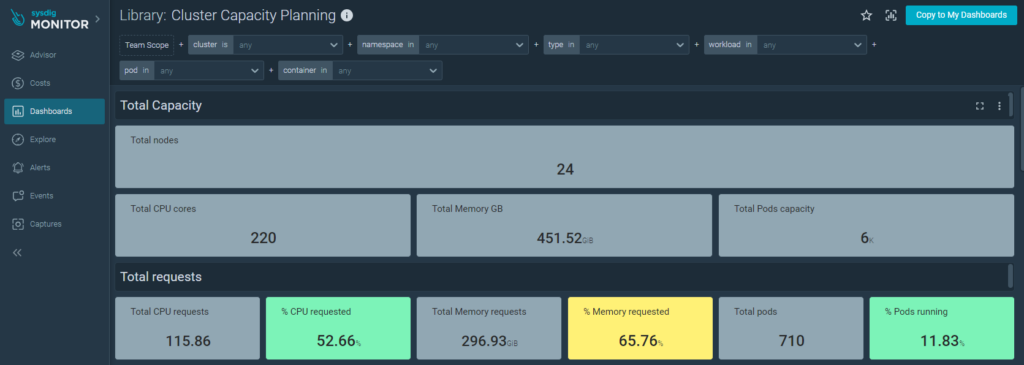
Capacity Planning:
Sysdig Secure operates on several layers and is dedicated to analyzing and mitigating security events relating to applications and infrastructure of the Kubernetes platform. There are policies that can be enabled in real time in order to mitigate possible security impacts on the environment. These policies can help prevent data leaks and other types of abuse.
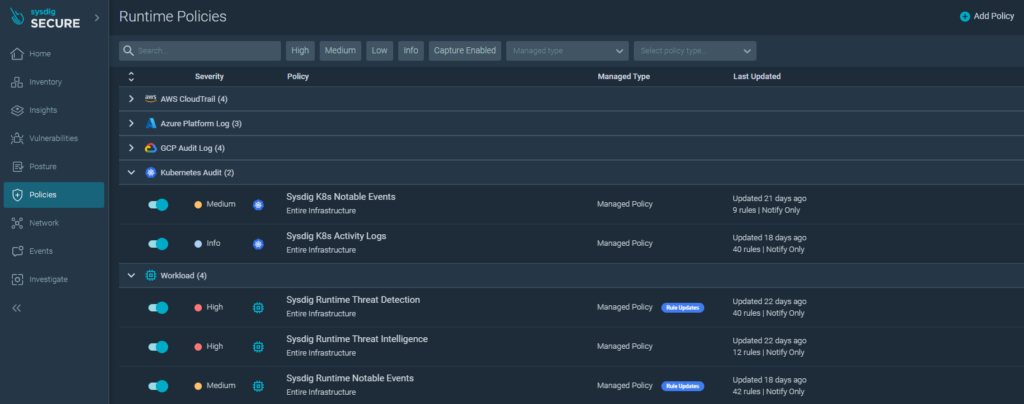
Real-time policies:
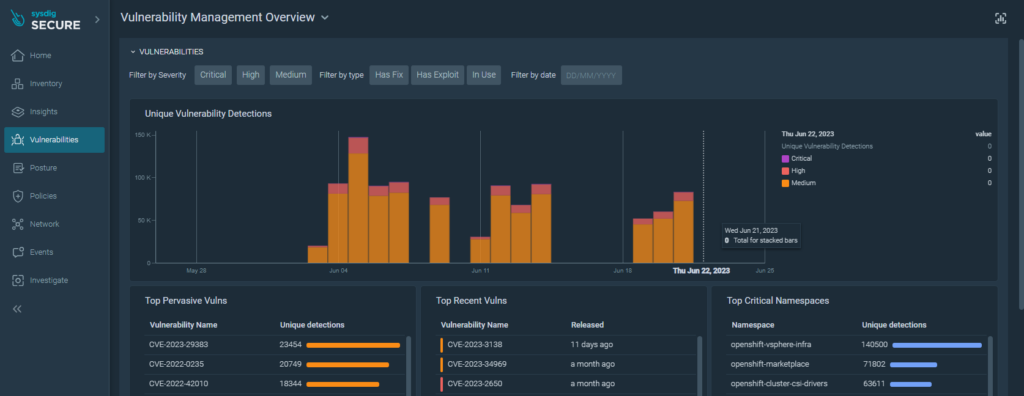
Insight into the vulnerabilities of the environment:
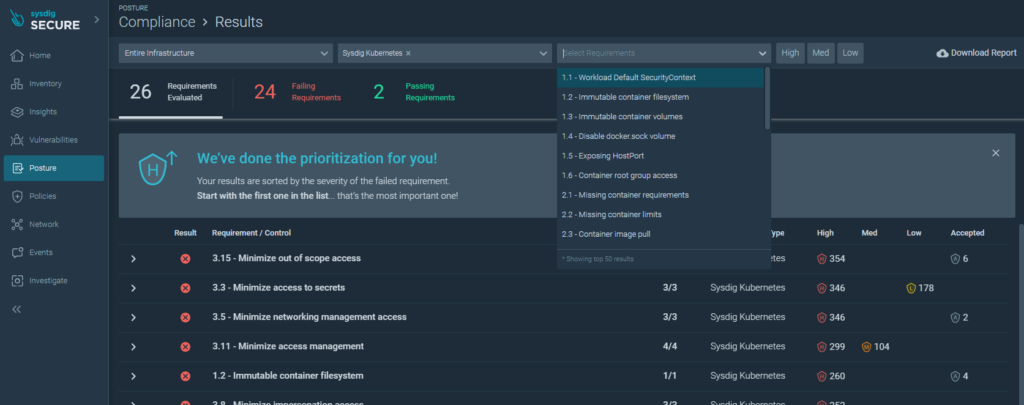
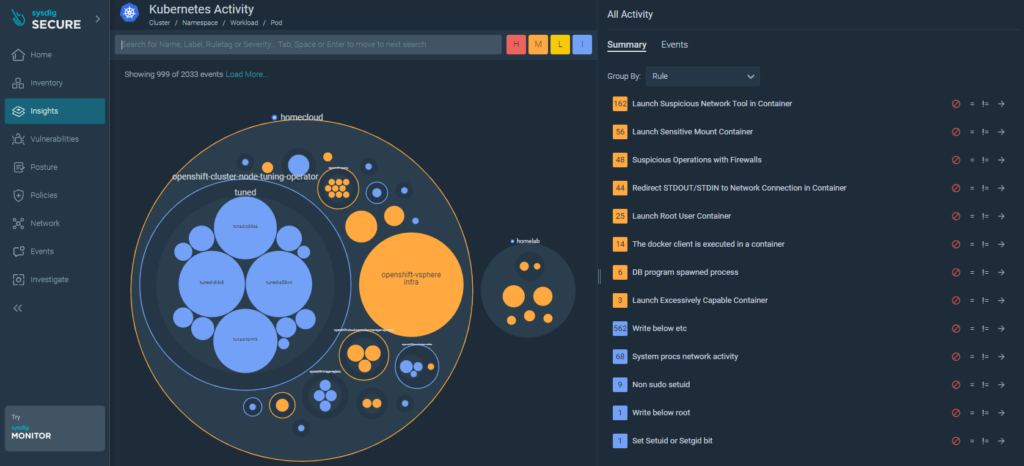
General insights:
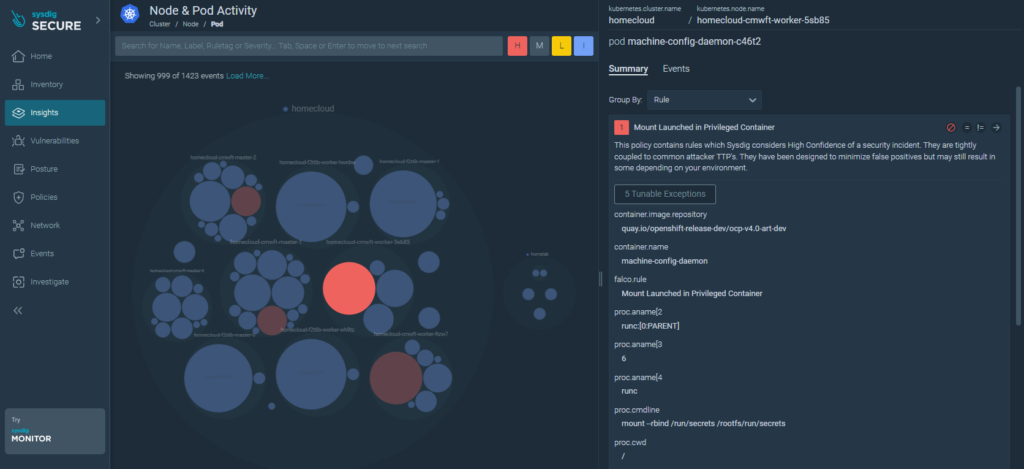
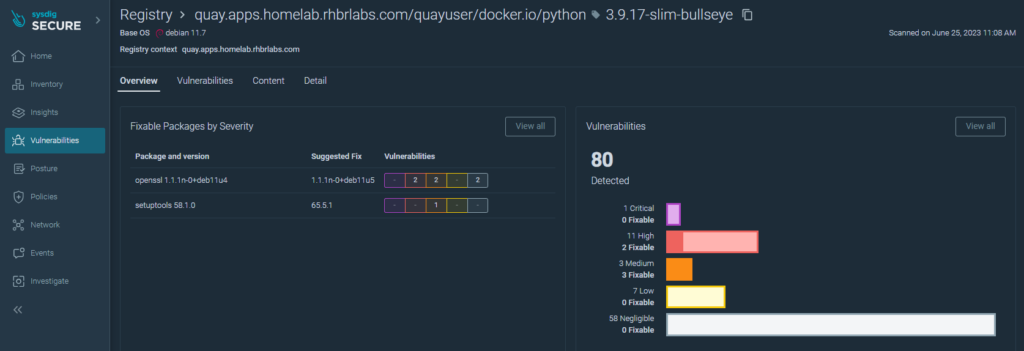
Normally kubernetes clusters are integrated with a registry solution. In this example, the registry solution in use is Quay.
Through integration, it is possible to analyze the stored images and search for those that are vulnerable and need to be adapted.
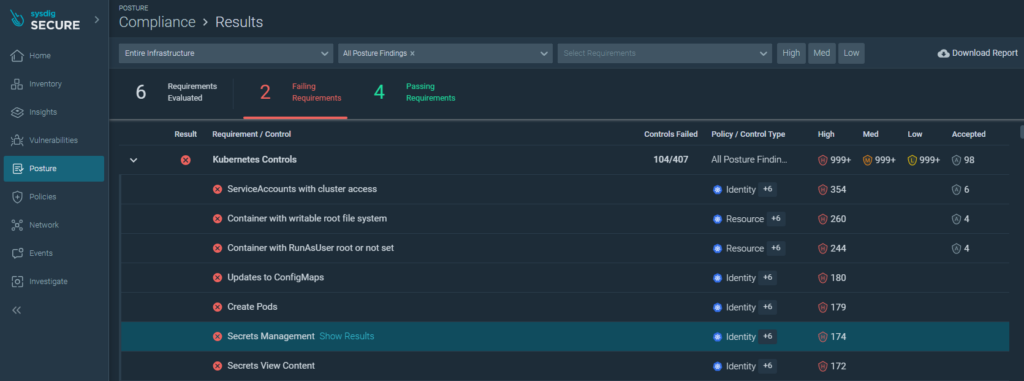
Overall security compliance is classified by severity level. This helps prioritize the activities that should be carried out to increase the level of security in the environment.
Real-time policies can be activated to proactively mitigate vulnerabilities and insecure configurations.
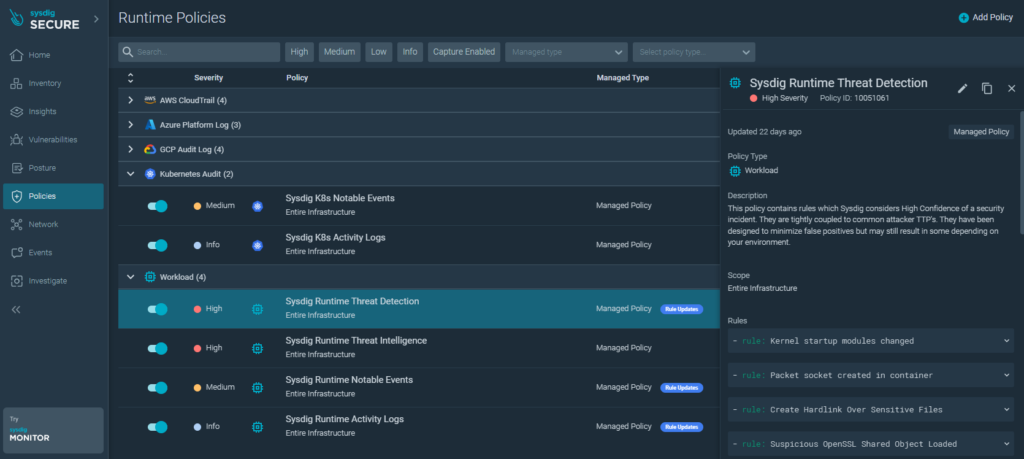
Ready to use policies act on the application layer and even on the base operating system of the nodes in the Kubernetes cluster.
There are countless other dashboards, configurations, integrations, policies and so on to explore!
In this article we’ve seen how interesting the Sysdig solution is, and how it can help combat security problems.
In the next articles, we’ll get to grips with how to install, configure and integrate Sysdig agents in a Kubernetes cluster.
Did you like the content? Check out these other interesting articles! 🔥
Do you like what you find here? With every click on a banner, you help keep this site alive and free. Your support makes all the difference so that we can continue to bring you the content you love. Thank you very much! 😊